Consulting
Adversarial attacks are focused and well planned. This sophistication is best addressed by a threat intelligence program that covers a variety of methodologies, strategies and tactics.
An effective intelligence program must address potential attacks from all domains including cyber, physical, human, technical and more. At Center for Threat Intelligence, we can assist you in building an effective threat intelligence program from starting with the basics, to reviewing your advanced threat intelligence programs and goals. We use our years of experience to develop programs that encompass the best strategy, tactics and processes for your organization.
Services include:
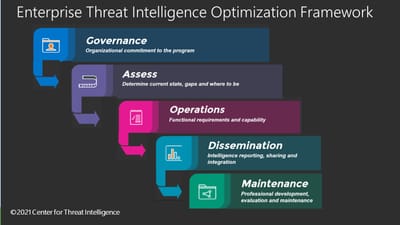
Enterprise Threat Intelligence Optimization Framework
A Holistic Approach to Corporate Wide Threat Intelligence
Adversarial attacks are increasingly sophisticated. To help companies address these evolving attack strategies, Center for Threat Intelligence created the Threat Intelligence Optimization Framework. Your adversaries have comprehensive strategies for your organization, you should too! We can help!
Benefits:
An effective intelligence program must address potential attacks from all domains including cyber, physical, human, technical and more. At Center for Threat Intelligence, we can assist you in building an effective threat intelligence program from starting with the basics, to reviewing your advanced threat intelligence programs and goals. We use our years of experience to develop programs that encompass the best strategy, tactics and processes for your organization.
Services include:
- Threat Intelligence Program Development
- Enterprise Threat Intelligence Assessment
- Enterprise Threat Intelligence Optimization Framework
- Insider Threat Program Development and Evaluation
- Threat Intelligence Program Evaluation
- Threat Analysis
- Strategy Development
Enterprise Threat Intelligence Optimization Framework
A Holistic Approach to Corporate Wide Threat Intelligence
Adversarial attacks are increasingly sophisticated. To help companies address these evolving attack strategies, Center for Threat Intelligence created the Threat Intelligence Optimization Framework. Your adversaries have comprehensive strategies for your organization, you should too! We can help!
Benefits:
- Synchronizes organization’s risk management, cybersecurity, physical security and other threat intelligence processes to enhance identification, early detection and mitigate risk from well-coordinated attacks.
- Provides coordinated communication to proactively inform management with critical, timely, contextual knowledge to assist in daily business decisions.
- Establishes the foundation for establishing a corporate-wide intelligence program.
- Increases ROI by decreasing duplication in security efforts, enhances communication for faster identification to stop credible threats and decreases costs associated with successful attacks.