Threat Intelligence Professional Services
Anticipating and preventing the next strike.
Threat Intelligence Program Development
Insider Threat Program Development and Training
Enterprise Threat Intelligence Assessments
Speaking Engagements
On Demand Training Courses
Certified Threat Intelligence Specialist Certification (CTIS)
Speaking Engagements

Janet Lawless
CEO and Founder Center for Threat Intelligence
Janet is CEO and Founder of Center for Threat Intelligence. Janet established a team of intelligence experts to build cutting-edge threat intelligence and insider threat programs, consulting, threat intelligence and insider threat training courses and a certification program for threat intelligence professionals.
Janet delivers engaging presentations at international conferences and corporate events. Known for her ability to engage her audiences through amazing real-life stories, her energy and enthusiasm for the topics is both thought provoking and fun.
In former leadership roles at Microsoft and Cisco, she created and managed global programs focused on compliance and security. In addition, she was the VP of Sales at a cybersecurity start-up and brings a wealth of knowledge in cybersecurity services.
Her engagements include presenting Insider Threat at the Overseas Security Advisory Council (OSAC) at the State Department and Lockheed Martin, to name a few. She is a keynote speaker and presenter at international conferences including ASIS International’s Global Security Exchange (GSX), SecureWorld conference, and speaks on a variety of topics including threat intelligence, insider threat and shares her personal story of motivation from teacher to CEO and how you can make a difference as she has, it just takes an idea, a little creativity, and not accepting no for an answer.
She is a member of the United States Secret Service Cyber Fraud Task Force, InfraGard (a partnership between the FBI and members of the private sector), and the Washington State Fusion Center. Janet is the Chair Emeritus for ASIS International Puget Sound Chapter (an international security organization), the Chair Emeritus for the Pacific Coast Analyst Roundtable and a former Board Member for the American Red Cross and Big Brother/Big Sister organizations.
She volunteers for the American Red Cross and Community Emergency Response Team (CERT), maintaining the attitude of in an emergency, you need to be part of the solution, not unprepared and part of the problem. Janet also founded “PCs 2 Vets” and has provided over 1,000 laptops to veterans.
Speaking Themes and Topics:
Threat Intelligence
Insider Threat
Motivational speaker
Customized topics
Contact Janet directly at jlawless@centerforti.com
On Demand
On Demand Courses
Certification

- Office of the National Counterintelligence Executive
Organizations are under attack from increasingly complex threats to their environments. Adversaries employ sophisticated attack strategies including cyber, physical, human and technology, often using a combination of these tactics. Experienced threat intelligence professionals employ holistic strategies, skills and techniques to proactively mitigate risk and ultimately eliminate surprise. Recognition of these valuable skills help excel your career as a business, security and/or threat intelligence professional.
APPLY FOR CERTIFICATIONS
Certified Threat Intelligence Specialist I (CTIS-I)
- Threat Intelligence Fundamentals course required. Pass assessment for certification. See below for more information.
- Designed for experienced intelligence professionals
- Pay for the Threat Intelligence Fundamentals START NOW!
- Go through the course
Threat Intelligence Fundamentals course begins the journey to the Certified Threat Intelligence Specialist I (CTIS-I) Certification. This course is intended for individuals looking to build their knowledge, experience and skills in the area of threat intelligence. Experienced threat intelligence professionals will use this course to validate their understanding of fundamental threat intelligence processes and concepts. Welcome to the world of threat intelligence, the adventure is waiting.
To get the CTIS-I certification: - At the end of the course, take the Threat Intelligence Fundamentals Assessment
- Pass the assessment and receive the Certified Threat Intelligence Specialist I (CTIS-I) Certification
- Passing score is 70% or higher
- You will receive a pass or fail score. Test questions will not be sent to you for review.
- The certification is included in the price of the course
Center for Threat Intelligence’s Certified Threat Intelligence Specialist II (CTIS-II) Certification
This certification acknowledges experienced intelligence professionals that understand intelligence tradecraft and recognize the importance of bringing cyber, physical, human, and technical pillars of threat intelligence into a comprehensive and integrated business strategy. The certification program was developed in collaboration with highly experienced intelligence experts with military, federal and corporate intelligence backgrounds, in order to provide a vehicle to demonstrate valued intelligence experience and skills.
Certified Threat Intelligence Specialist II (CTIS-II)
Requirements:
- Pass CTIS-II Certification Examination ($395.00)
- Passing score is 70%
- You will receive a pass or fail score. Test questions will not be sent to you for review.
- Agree to Certification Code of Professional Conduct
We are honored to be an education and training provider for the Department of Homeland Security's National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework (NICE Framework), published by the National Institute of Standards and Technology (NIST) in NIST Special Publication 800-181.
Why become a Certified Threat Intelligence Specialist?
Certified Threat Intelligence Specialist certification benefits you by:
- Recognizing your current knowledge: The certification identifies your years of unique experience and training to showcase your understanding and use of intelligence in any organization to enhance business decisions, anticipate sophisticated threat strategies and prevent attacks from being successful.
- Enhancing your career: This certification demonstrates the necessary knowledge to enhance your business knowledge of threat intelligence and enhance your current skills to build a holistic approach in your organization. This may assist in current and future employment opportunities.
- Expanding your skills and knowledge: Take on added responsibilities and gain additional respect and opportunities from clients, peers and employers.
- Becoming a part of a unique and highly respected intelligence community.
- Providing opportunities to learn from intelligence experts, they are your instructors: Our instructors have years of threat intelligence experience in military, federal agencies and corporate environments. They have faced the challenges and have developed insight, tactics and strategies to address them. They understand the skills need to do the job; this ensures the content prepares you for what is needed in the market.
Who should get certified?
- Security and Intelligence Professionals: Enhance skills to understand adversarial focus, apply threat intelligence practices to current and future roles, understand how critical thinking enhances analysis, improve structured analytic techniques and sensemaking skills.
- Attorneys: Establish knowledge and understanding of how threat intelligence can enhance legal activities, such as investigation and your clients.
- Managers and Executives: Understand threat environments to prioritize and address risk. Helps communication with threat intelligence analysts to ensure communication is open and effective when communicating needs.
- Risk, Compliance and Human Resource Professionals: Understand and prioritize insider threats and enhance knowledge of potential risks before they happen.
- Federal Agents and Law Enforcement: Master threat intelligence techniques for advanced investigations improving job skills.
- Students: Start a career as a Certified Threat Intelligence Specialist I.
Eligibility Criteria
Due to the COVID-19 pandemic, all testing and training will be online until further notice.
Thank you for your patience and support.
In order to be eligible for the CTIS-II examination, an individual must:
- Pay the Application Fee for the Examination or Retake Fee if retaking the exam. All fees are non-refundable.
- Agree to Center for Threat Intelligence's Certification Code of Professional Conduct.
Process
Once application is paid, you can take the Certification Exam. Once completed, simply submit the test. You will receive a pass or fail score. The test will not be returned to participants for review. Upon passing, Center for Threat Intelligence will send you your CTIS-II Certification Certificate.
Fees
All candidates are required to pay the $395.00 application fee to take the Examination. This fee includes one examination.
Retake fees: $100.00
Please review all the eligibility requirements before applying and paying the application fee.
All Fees are non-refundable.
Please note, the Application fee is only for the CTIS-II examination, training courses may be purchased separately.
APPLY NOW!
Certification Code of Professional Conduct
Center for Threat Intelligence (CTI) expects our certified members to adhere to and maintain the highest ethical and professional standards. To that end, CTI has professional standards that eligible candidates and current certified members must agree to as part of the certification criteria.
CTIS-II applicants must adhere to the Code of Professional Conduct agreeing to:
- Respect the Law and comply with all laws and regulations. Perform professional duties in accordance with the law and the highest moral and ethical principles.
- Adhere to conduct of truthfulness, honesty, and integrity
- Perform professional duties maintaining the highest standards of competence and knowledge
- Respect and safeguard confidential and privileged information and exercise due care to prevent its improper and/or accidental disclosure
- Respect the professional reputation or practice of colleagues, clients, or employees
- Agree to abide by the Certification Code of Professional Conduct
The test is 75 questions. Test questions are based on Center for Threat Intelligence training and suggested reading. A score of 70% of correct answers is considered a passing score. You will receive a pass or fail score. The test will not be returned to participants for review.
Recommended Training from Center for Threat Intelligence
- Threat Intelligence Fundamentals
- Mindset and Bias
- Critical, Analytic and Creative Thinking
- Structured Analytic Techniques
- Sensemaking
- The Behavioral Psychology of the Insider Threat: How to Identify and Mitigate
- Structured Analytic Techniques for Intelligence Analysis, Second Edition, by Richards J. Heuer Jr. and Randolph H. Person
- Sensemaking A Structure for an Intelligence Revolution, David T. Moore, National Defense Intelligence College, Washington, DC, March 2011
- Intelligence: From Secrets to Policy: Mark M Lowenthal
About
Your organization faces constant risk. Adversaries are sophisticated, clever and focused. Attacks are well planned, coordinated and use a variety of tactics including cyber, physical, human and technical to accomplish their goals.
Center for Threat Intelligence benefits organizations by using proven methodologies to create holistic, integrated and proactive intelligence programs. Our experienced consultants help you build successful threat intelligence programs to proactively identify who your adversaries are and where they are focused. Adding intelligence to your business decisions and risk management process, gives your organization cutting edge knowledge to create an early warning system to manage and mitigate risks before a strike.
Applied throughout an organization, our intelligence framework can benefit every business discipline including risk management, information security, legal, human resources, management and executive and board level positions.
We offer comprehensive consulting services, training and certifications to address the needs of our clients. From security practitioners developing basic knowledge to advance skills in threat intelligence, to executives looking for a high-level understanding on the benefits of early warning intelligence.
Contact us today!

Advisors
CEO and Founder
Janet Lawless is the CEO and Founder of Center for Threat Intelligence. Collaborating with threat intelligence experts, Janet realized the need to help organizations design holistic threat intelligence programs which includes building resources through threat intelligence consulting, training and certifications for corporations and government organizations. Janet’s former roles in leadership positions at CI Security, Cisco and Microsoft brings a wealth of knowledge in security services and the need for threat intelligence.
Advisor
David Aucsmith is a senior computer scientist and technology leader currently working as the Chief Scientist and Federal Practice Manager for DarkLight and as a Senior Principal Research Scientist at the Applied Physics Laboratory of the University of Washington. He is also an Affiliate Professor of Computer Science & Engineering at the University of Washington. He has worked in a variety of security technology areas including secure computer systems, secure communications systems, security architecture, random number generation, cryptography and cryptographic systems, steganography and network intrusion detection.
Advisor
Collin Barry is a senior leader in Expedia Group's Security Enterprise responsible for building a next-generation cyber threat intelligence capability. Prior to Expedia Group, Collin was living in Singapore where he led Booz Allen Hamilton's cyber practice for the Asia-Pacific region. Mid-career, Collin worked as an Intelligence Analyst at the Central Intelligence Agency, where he garnered deep expertise in intelligence support to real-world mission operations.
Advisor
David Gomez is a retired FBI executive, security consultant, and cybersecurity professional with practitioner experience in complex, high-risk, critical incident management and response. He is a former Senior Fellow at the George Washington University Center for Cyber and Homeland Security, and frequent media contributor on law enforcement, cybersecurity, and counterterrorism topics.
Advisor
Bryan is a seasoned cybercrime, computer security and homeland security professional with over 20 years of experience. He is an accomplished organizational spokesperson, public speaker and advisor to CxO level and national level executives. Bryan’s unique ability to apply very positive and transparent leadership to direct teams of investigators, developers, data scientists, data visualization experts, and other professionals make him an excellent addition to the Center for Threat Intelligence Advisory Team.
Advisor
Jim is currently a board member at Overlake Hospital Medical Center and is a past board chair of Seattle Children’s Hospital, the Washington Society of CPAs, and the Duke Alumni Association, among roles at many other boards. Previously Jim had a successful career at Deloitte, an international accounting and consulting firm, where he served as managing partner of the Seattle office, the Tokyo office, and worldwide human resources, along with important client assignments.
Advisor
Oriah currently leads the cybersecurity and threat intelligence programs for SkOUT Secure Intelligence throughout the western United States. He also serves on several non-profit and private company boards in both a director and advisory capacity. Previously, he served in the U.S. Air Force for over 21 years on Active Duty and continues to serve part-time in the Air National Guard. He began his military career as an enlisted Communication Analyst overseas with the National Security Agency.
Advisor
Greg currently leads the Uber cyber-threat intelligence team and developed the Uber global threat intelligence strategy. He supports multiple groups including legal, executive protection, incident response, third party risk and others. Greg developed and delivered a threat intelligence training program to extend threat intelligence capabilities across the enterprise.
Advisor
Guy Shinnar is the Director of Sales US West, for Check Point Software Technologies, Ltd. Guy has unique experience in the security industry with US, and international executive roles. These include his roles as Co-Founder and VP of Sales at Eemago and Director of Sales at Panaya (acquired by Infosys) an internationally recognized start-up. Guy also co-founder and CEO at Gaash Security Training and Consulting LTD focusing on physical security solutions for government and civilian facilities. In the military, Guy served as Captain, Special Forces, Israel IDF.
Advisor
Joel is currently a Principal Product Manager for Security and Risk Management at Veritas Technologies. He recently retired from active duty after 20 years as an Intelligence Officer in the United States Air Force. Over the course of his military career, Joel served in multiple intelligence and risk management leadership roles. Most recently as full-time faculty member in the College of Science and Technical Intelligence at the National Intelligence University in Washington DC. He taught graduate level courses on threat intelligence and cybersecurity.
Consulting
An effective intelligence program must address potential attacks from all domains including cyber, physical, human, technical and more. At Center for Threat Intelligence, we can assist you in building an effective threat intelligence program from starting with the basics, to reviewing your advanced threat intelligence programs and goals. We use our years of experience to develop programs that encompass the best strategy, tactics and processes for your organization.
Services include:
- Threat Intelligence Program Development
- Enterprise Threat Intelligence Assessment
- Enterprise Threat Intelligence Optimization Framework
- Insider Threat Program Development and Evaluation
- Threat Intelligence Program Evaluation
- Threat Analysis
- Strategy Development
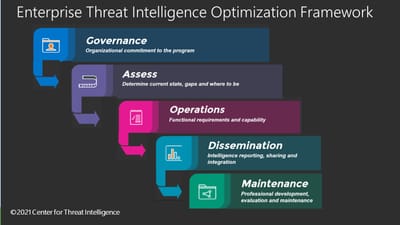
Enterprise Threat Intelligence Optimization Framework
A Holistic Approach to Corporate Wide Threat Intelligence
Adversarial attacks are increasingly sophisticated. To help companies address these evolving attack strategies, Center for Threat Intelligence created the Threat Intelligence Optimization Framework. Your adversaries have comprehensive strategies for your organization, you should too! We can help!
Benefits:
- Synchronizes organization’s risk management, cybersecurity, physical security and other threat intelligence processes to enhance identification, early detection and mitigate risk from well-coordinated attacks.
- Provides coordinated communication to proactively inform management with critical, timely, contextual knowledge to assist in daily business decisions.
- Establishes the foundation for establishing a corporate-wide intelligence program.
- Increases ROI by decreasing duplication in security efforts, enhances communication for faster identification to stop credible threats and decreases costs associated with successful attacks.

Training
An innovative, customized course designed to improve the de-escalation and decision-making skills of law enforcement within the framework of the Guardian mindset in situations characterized by ambiguity, uncertainty, unpredictability, changeability, time-pressure, competing or changing goals, and potential danger. Customized online learning to meet your individual training and scheduling requirements. Online course includes: • Introductory video explaining course objectives, themes, decision-making theory, and the ShadowBox methodology. • Eight experiential ShadowBox training exercises. Each exercise requires trainees to make and explain numerous challenging decisions before being exposed to insights from select Subject Matter Experts (SMEs) regarding those same decisions. • Flexible scheduling – Courses are online and on-demand to meet scheduling requirements.
Information is everywhere. With the proper training, the right information can be found and transformed into actionable intelligence and valuable insight to help companies and law enforcement detect and mitigate risks. In this course, and hands-on workshop, students will learn the tools and techniques used in the field of Open Source Intelligence (OSINT). With special emphasis on social media monitoring, the training is designed to enable security professionals and law enforcement to better discover and evaluate threats, and to conduct efficient and effective online investigations.
The Center for Threat Intelligence has partnered with People Formula to bring you this intriguing course, we examine the behavioral psychology of the insider threat. We'll uncover critical signs, underlying motivations and dive into what makes a person become an insider. Insiders are motivated by many things. We'll discuss critical behavioral signs and the psychology that drives them. Most importantly, we will review how to identify and mitigate the potential insider threat.
Organizations are under attack from increasingly complex threats to their environments. Adversaries employ sophisticated attack strategies including cyber, physical, human and technology, often using a combination of these tactics. Using threat intelligence skills and techniques allows you to proactively defend your environment by understanding adversarial strategy, identifying potential targets and ultimately eliminate surprise. These valuable skills will help excel your career and begin your journey to becoming a Center for Threat Intelligence Certified Threat Intelligence Professional. The first step in building a career in threat intelligence is Threat Intelligence Fundamentals.
Check out our new On Demand Section for online courses.
You know just about everything there is know about intelligence or physical security. And then the cyber people show up. They talk in a way that's almost incomprehensible and what do those acronyms even mean? Their language is so weird that you're not even sure how to ask smart questions. That's not setting you up for success. In this session, we'll explain cyber in ordinary language so you can navigate future cyber conversations without the road blocks, confusion, and false starts. Training session are three one-hour courses starting December 14th, 16th and 18th at 11:00 am PST. Price includes all three sessions. Exclusive one-time introductory course pricing.
Insider threats can devastate an organization. These threats are often hard to detect and are caused by negligent insiders, malicious insiders and/or external actors who infiltrate an organization. Insiders may be current or former employees, contractors, vendors, or trusted third parties. Insider attack strategies including cyber, physical, human and technology, often using a combination of these tactics. Motivations can be anything from financial gain to wanting to disrupt operations to get back at the company because of a bad review or missed promotion. Using threat intelligence skills and techniques to understand insider threats allows you to proactively defend your environment. Center for Threat Intelligence is an approved provider for Department of Homeland Security’s (DHS) National Initiative for Cybersecurity Careers and Studies (NICCS) and the National Initiative for Cybersecurity Education (NICE).
Threat intelligence continues to gain a more prominent role in enhancing organizational security and risk management. A critical part of threat intelligence is understanding how mindset and biases play a role in strategies, tactics and vital decisions that may ultimately prevent an attack from being successful. Perception and deception are effective adversarial tactics, knowing your own and your team’s mindsets and biases can assist in getting ahead of the game. Center for Threat Intelligence is an approved provider for Department of Homeland Security’s (DHS) National Initiative for Cybersecurity Careers and Studies (NICCS) and the National Initiative for Cybersecurity Education (NICE).
Organizations are under attack from increasingly complex threats to their environments. Adversaries employ sophisticated attack strategies including cyber, physical, human and technology, often using a combination of these tactics. Using threat intelligence skills and techniques allows you to proactively defend your environment by understanding adversarial strategy, identifying potential targets and ultimately eliminate surprise. These valuable skills will help excel your career and begin your journey to becoming a Center for Threat Intelligence Certified Threat Intelligence Professional. The first step in building a career in threat intelligence is Threat Intelligence Fundamentals.
Today’s global threats by sophisticated actors, nation-states, organized crime and hacker groups, are highly complex. Many of these threats can be related to a variety of events that seem to have no correlation, yet are drivers and indicators of an imminent attack on your organization. Understanding the next attack, where it will hit and when, are intelligence questions that simply have no black and white answers. These complex problems, also called “wicked problems”, need advance thought processes, techniques and tools, they need “Sensemaking”.
With new expectations and responsibilities being placed on law enforcement and organizations, understanding the fundamentals of threat intelligence is critical to every situation. Using processes within the threat intelligence framework allows you to proactively defend your environment and understand adversarial strategy and potential targets. This knowledge will also assist in making decisions based on identifying real risks and prioritizing resources to address them. The first step in building a proactive security environment is creating a foundation for threat intelligence.
This course provides an in-depth look at Structured Analytic Techniques (SATs) for intelligence analysis. Analysts face many obstacles in developing intelligence, some of which are introduced through human mindsets and biases. Mindsets and biases further complicate the analysis process and often impact an analyst's judgement. SATs are a series of analytic techniques that help reduce mindset related problems with analysis and provide for a structured and organized process for evaluating and analyzing intelligence. The results are more accurate analysis, a way for an analyst to validate evidence, assumptions and analytic leaps and show how an analyst came to a certain judgement.
Thinking processes play a key role in threat intelligence. Understanding how these processes impact the analysis can improve the effectiveness and outcome of the process. This course analyzes different thinking methods and teaches students how to apply these methods in intelligence analysis. Each thought process has pros and cons related to differing problem types and how problems, whether tame or wicked, are approached. Analysts will benefit by understanding which thought process is most effective for their style of thinking and how to best exploit each of the three methods as part of a problem-solving process.
Threat intelligence can be affected by a number of factors. It is essential to understand how thinking processes play a key role in the effectiveness of intelligence analysis. This course analyzes different thinking methods and teaches students how to apply those methods in intelligence analysis. Each thought process has pros and cons related to differing problem types an example being problems that are tame or wicked. Analysts must also understand which thought process is most effective for their style of thinking and how to best exploit each of the three methods as part of a problem-solving process.
Threat intelligence allows you to take proactive measures in defending your environment and understand adversarial focus and what it means to an organization. This course will give you an understanding of mindsets and biases that can lead to incorrect judgements in intelligence analysis.
Threat intelligence continues to gain a more prominent role in enhancing organizational security and risk management. Using processes within the threat intelligence framework allows you to proactively defend your environment and understand adversarial strategy and targets. This knowledge will also assist in making decisions based on identifying real risks and prioritizing resources to address them. The first step in building a proactive security environment is creating a foundation for threat intelligence.
Courses Offered

Threat Intelligence Fundamentals + Certification
Threat Intelligence Fundamentals offers core knowledge and skills for professionals interested in better understanding threat intelligence and how to apply these skills and techniques to everyday responsibilities. Using processes within the threat intelligence framework allows an organization to proactively defend their environments, understand adversarial strategy and targets, and use this knowledge to make business decisions based on identifying real risks and prioritizing resources to address them. The first step in building a proactive security environment is creating a foundation for threat intelligence. This training provides attendees with a foundational understanding of threat intelligence. Students begin their journey into the tradecraft of intelligence and how to build a holistic approach to anticipating and preventing attacks.
Learn More
Managers and Executives
The manager and executive courses are specifically designed to introduce managers and executives to the important role intelligence plays in risk management and security.
Learn More
Customized Corporate Training
A well trained team can provide the excellent skills and expertise to keep your organization secure. We provide customized training courses for your team's needs.
Learn More
Course Offerings
Our courses focus on critical threat intelligence skills. These skills include how to develop meaningful sign-posts, making sense of global threat trends and patterns, cyber-intelligence strategies, identifying and prioritizing risk and much more. See below for a list of available courses.
Learn More
For Law Enforcement
The Guardian Mindset: De-escalation and Tactical Decision Making is an innovative, customized course designed to improve the de-escalation and decision-making skills of law enforcement within the framework of the Guardian mindset in situations characterized by ambiguity, uncertainty, unpredictability, changeability, time-pressure, competing or changing goals, and potential danger.
Learn MoreContact
- Seattle, WA, United States